In February 2022, electric car drivers on the M11 between Moscow and St. Petersburg were met with unexpected messages at several charging stations: "Honor to Ukraine" and "Putin is an idiot", it was written on the screens and the poles could not be used either.
According to the Russian energy company Rosseti, a Ukrainian company had manufactured one of the main components, and had taken advantage of a backdoor to temporarily shut down the poles.
In Sweden, there are now 60,000 charging connections for the public.
– In many cases, perhaps one does not think about security first, but rather rushes to get out the charging infrastructure, says Andreas Gotthardsson, cybersecurity expert at Fortinet.
Critical infrastructure
Mikael Asplund, who researches security and reliability for cyber-physical systems, is on the same track.
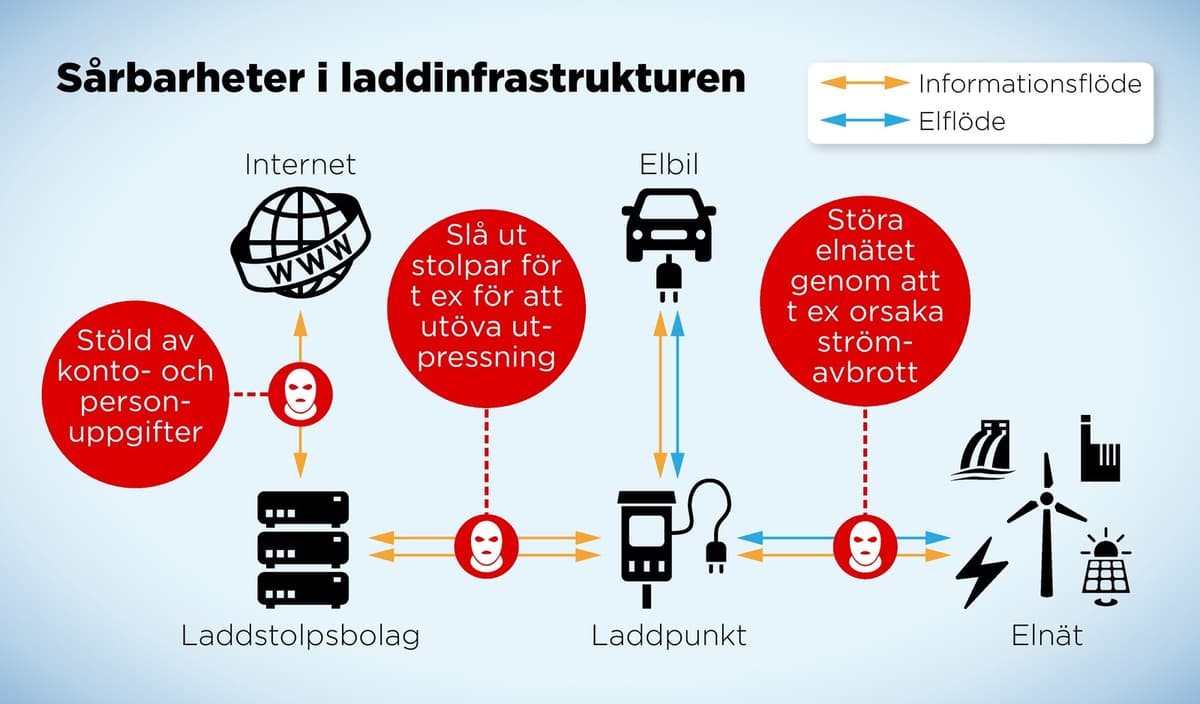
Charging stations are part of our critical infrastructure, both power grids and transportation.
Together with a couple of colleagues investigated he a few years ago the security of charging stations, and saw several deficiencies:
It can be quite easy to shut down these, to make them unavailable, he says.
If all charging stations in a certain area do not work when many normally charge, the cars can become stationary.
Then it can become a disruption to society, he says.
Attacks on the power grid
Even more serious is that charging stations could be used for attacks on the power grid.
If you turn on or off a large number of charging stations at the same time, you can trigger different types of protection mechanisms that cause the power to be turned off, at least in some areas.
Charging stations are based on technology from several different suppliers. It is actually enough with a deficiency in one of the steps for a malicious actor to be able to exploit it.
For the customer, it could mean interrupted charging, longer waiting times, incorrect billing or leaked personal data, says Gotthardsson.
When Mikael Asplund and his colleagues got in touch and pointed out the deficiencies, the manufacturers blamed things like the software not being updated, and that it was someone else's responsibility.
It is a bit symptomatic of security work – that there is a reluctance to take on security problems because one does not want to be associated with it, he says.
+ Disrupt the power grid. If hackers take control of a large group of charging stations, for example via a central control system, they can be used to cause power outages.
+ Shut down the poles. Customers cannot use them. Can cause major problems at times when many are charging, and can be used to disrupt or extort pole owners.
+ Access data. Charging station companies can collect customer data such as sensitive personal data, information about when and where the customer's car has been charged, as well as credit card information.
+ Steal money. Hackers can redirect traffic to fake payment sites to steal money. This can, for example, happen by pasting fake QR codes on charging stations.
+ Dutch researchers showed last year that you can often bypass network protection and directly access internal services via the charging cable.
+ Charging stations should preferably be connected to closed private networks. But some are openly searchable in databases on the internet and thus vulnerable.